HTTP basic authentication
HTTP basic authentication
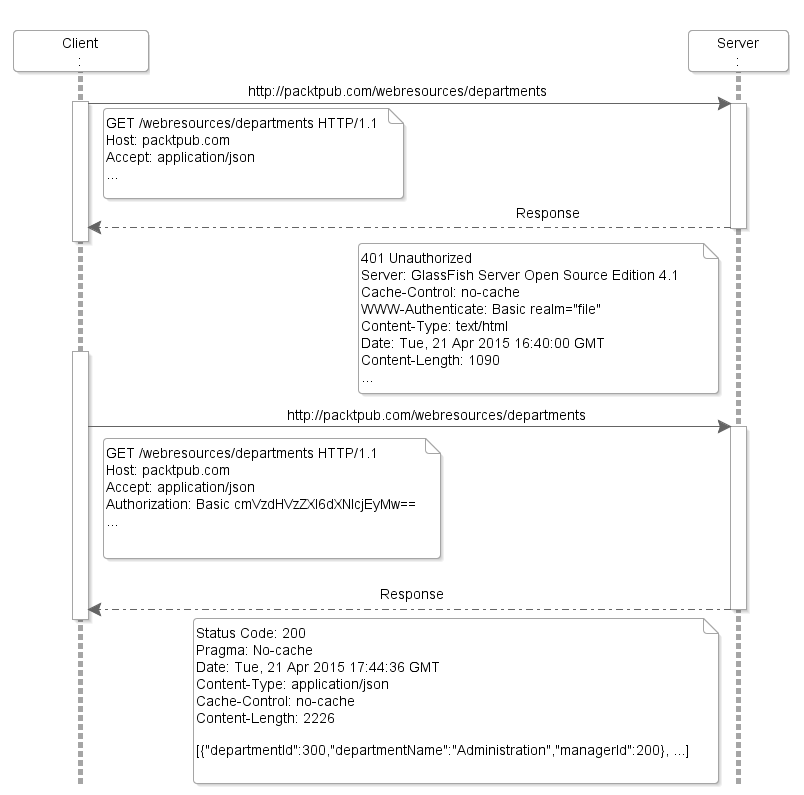
The preceding diagram represents an entire transaction. A client begins by requesting the URI, /webresources/departments. Because the resource is secured using HTTP basic authentication and the client does not provide the required authorization credentials, the server replies with a 401 HTTP response. The client receives the response, scans through it, and prepares a new request with the necessary data needed to authenticate the user. The new request from the client will contain the authorization header set to a Base64-encoded value of column-delimited username and password string, <username>:<password>. This time, the server will verify the credentials and reply with the requested resource.
As you have seen earlier, client requests can be generated from any application that can create HTTP connections, including web browsers. Web browsers typically cache the credentials so that the users do not have to type in their login credentials for every secured resource request. This is viewed as a deficiency of the protocol, since unauthorized access can take place with cached credentials, and there is no way for a web service to differentiate authorized requests from the unauthorized ones. Also, the login credentials can be easily deciphered as they are Base64-encoded. However, the intent of Base64 is not to secure the name-value pair but to uniformly encode the characters when transferred over HTTP. Because of these reasons, it is not recommended to use basic HTTP authentication for any application accessed over the internet. In general, we solve this potential security hole by using HTTPS (transport layer security) instead of HTTP, which we will discuss later in this chapter.
Comments
Post a Comment